A Cure Worse than the Disease
The upsurge of cybersecurity risks grew in unison with the rise of connected vehicles. What if consumers had the ability to kill the connection to the cloud? Would it stop the hackers? Could it make connected cars safer?

For the past two years, and counting, the world has been wrestling with COVID-19 and debating the most appropriate pathway back to normality. We have witnessed round after round of dueling experts, posturing politicians, clashing subcultures and well-founded anxiety amongst the general population. In such circumstances it is natural to grasp onto the promise of a quick and easy fix. However, these don’t tend to exist and pursuing them invariably causes more harm than good.
Despite the suite of benefits connected cars offer, drivers remain understandably anxious about the security risks attached to vehicle connectivity. According to Deloitte, globally more than 60% of connected car drivers in 2021 are concerned about someone hacking their vehicle and creating a risk to their safety.
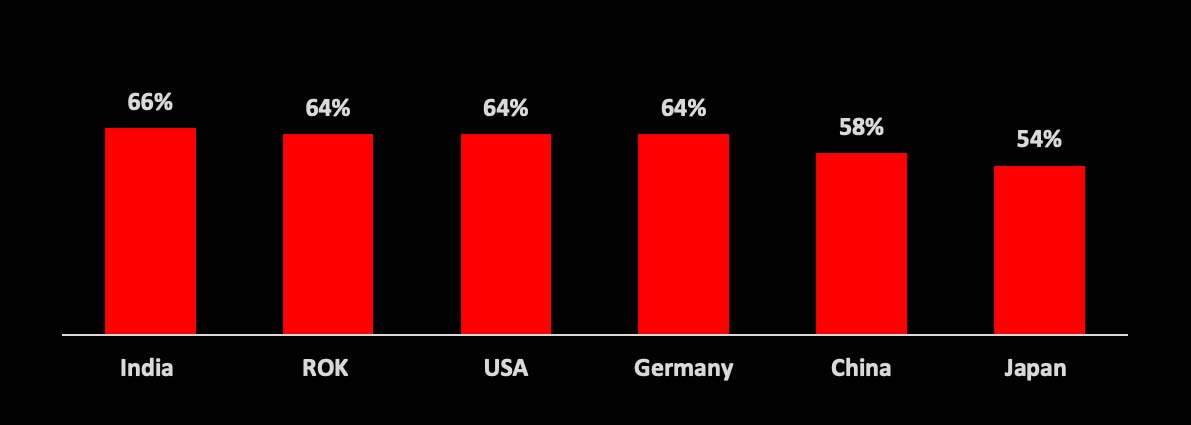
(Deloitte 2021 Global Automotive Consumer Study)
In 2019, Consumer Watchdog published an investigative report detailing rising concerns surrounding connected vehicles – aptly named the “Kill Switch” report

The front page asserted that “connected cars can be killing machines”, alongside several images of multi-vehicle accidents. Heady stuff! But let’s pause for a moment to ask: how and why was the idea of a kill switch conceived?
The upsurge of serious cybersecurity risks grew in unison with the rise of connected vehicles (as discussed in our previous post), so the ability to kill this connectivity and allow consumers to prevent themselves from being hacked would only be sensible, right? Unfortunately, it’s not that simple, and the kill switch comes laden with drawbacks, as follows.
1. It creates consumer distrust
The mere presence of the switch implies that the manufacturer has not been able to sufficiently address the cybersecurity risks and has proceeded with an unsafe design. In discouraging purchasers, the actual impact of the kill switch would not be cents added to each vehicle’s production cost, but thousands of dollars lost on a failed sale.
2. It only stops “movie” hacks
The kill switch seems to have been designed to thwart TV and movie hackers, and it would not be very effective against real-world attacks. On the screen, the victim often receives subtle warnings and time to anticipate an attack. The instruments may act strangely, the victim might struggle to gain control the vehicle, the lights inside the cabin might flash on and off. This is fantasy. Genuine attacks are not planned with cinematic tension in mind. Threats may be executed almost instantly without warning. The victim wouldn’t have time to reach the switch, let alone use it to disconnect communications. Real-world attacks rarely rely on ongoing end-to-end connectivity, as depicted by Hollywood. Detecting a real attack and then interrupting the communications while the attack is occurring would do little to prevent harm.
3. It’s counterproductive
Critical safety systems rely on vehicle connectivity. Systems like E-Call (Emergency Call Assistance) automatically alert emergency services in the event of a collision. A kill switch that severs all communications and disables systems like E-Call, would increase the likelihood of death in the event of a serious collision by delaying the arrival of emergency services. Connectivity is also improving OEM's diagnostic capabilities to identify attacks, and deliver over-the-air real time updates. This allows rapid mitigation of vulnerabilities without the expense and inconvenience of vehicle recalls.

4. There are better solutions
Standard automtive safety requires supervisory functions that monitor the behaviour of safety critical systems. These can also enforce minimal safe behaviour of systems which are exposed to connectivity risks. This best-practice attack-tolerant architecture is a clear responsibility in current vehicle cybersecurity standards and regulations. Focusing on compliance with these design standards will deliver a more expansive and secure solution than a connectivity kill switch.
Don't shoot the messenger
Kill switches aren’t the answer. Instead, manufacturers need to embrace connectivity and leverage its positive capabilities. They also need to establish a clear, well communicated strategy that addresses safety and cybersecurity concerns of consumers. Those who can achieve both these things will not only win the trust of consumers, but also gain a significant market advantage.
